Analyzing Uncertainties, Tehzun Kachwala, Kettan Sharma, Pratik Patil, Gurjinder Singh [ebook reader with internet browser txt] 📗

- Author: Tehzun Kachwala, Kettan Sharma, Pratik Patil, Gurjinder Singh
Book online «Analyzing Uncertainties, Tehzun Kachwala, Kettan Sharma, Pratik Patil, Gurjinder Singh [ebook reader with internet browser txt] 📗». Author Tehzun Kachwala, Kettan Sharma, Pratik Patil, Gurjinder Singh
It is the result after every performance which gets prioritized according to their overall effect on project.
We get the updated risk report which has the risks prioritize according to overall effect on project.
So, the let’s see the example from below table which is our previous case study in which we made risk register according to the overall effect on project which is seriousness of risk in this table and its color graded for quick look.
Risk Register
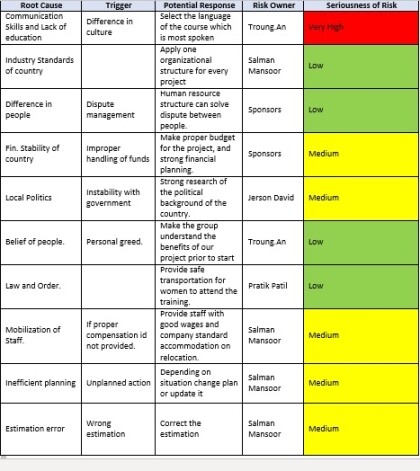
Table :Risk Register
Plan Risk Response
It is process of Developing options, selecting Strategies, and agreeing upon the actions to address overall project risks exposure as well as to treat individual project risks. The key benefit of this process that it identifies appropriate ways to address overall project risk and individual project risk (PMI, 2017).
This process is most important as knowing risk is not going to solve the problem but effectively handling them will solve the problem and unsuitable risk response can have converse effect.
So now let’s see the risk response strategies which are mostly used and discuss them in brief:
Escalate: Escalation is the appropriate solution when project manager or sponsor things are agreed that the threat from the risks is beyond preparing for so they remove the risks responsibility for consequences to the other party.
Example: when we take house insurance we know if house gets burned, we cannot afford it to repair so we escalate that risk to insurance company.
Avoid: Avoiding is the strategy when the impact of the risks and the probability of it happening is high, so the team decides to change the project plan so that that risks can be avoided and the effect of that risks is low or completely been removed from the project. This strategy can be used when the project team can change that scope from the plan.
Example: when you are buying a used car and its engine is been opened then it means that probability for failure of engine in future is high and cost is high, so you don’t buy that car and instead you go for better option.
Transfer: It is same as escalation only thing is that you can give that work to some other party or pay them the amount for that risk.
Mitigate: In mitigation what do you do here is take actions to reduce the probability of occurrence and or impact of the threat. here you do is you act early on for the risk so that the impact of risk is reduced to applicable amount. Also, you ensure that the probability of risk is also been reduced by large amount it is very important that from the two of the factors probability and impact you should be able to reduce at least one of them.
Accept: Here you do is that you accept the risk and you can afford risk. If it is positive risk or opportunity it is easy to accept.
Exploit: Mainly consider the positive risks and the probability of it happening and try to gain more from that risks.
Share: The positive risk is an opportunity to share the benefit with the vendor or your partner so that in future you get the trust from the vendors. It also involves sharing of payment or the money you get from the positive risk and it is the both ways.
Process of implementing agreed upon risk response plans, we need to apply the plans according to how we are planning it. Most important factor for risk is implementation and that matters a lot for the project. Project risk requires the implementation implemented in correct time. It is also called as mitigation plan. (PMI, 2017)
Process of Implementing Risk Response:
Risk Event Occurred: we only implement the risk response when the risk event occurs. It cannot be implemented without the indications of the event occurred so that we don't waste resources on that and it is very much important to consider it. As soon as the event occurs, we start implementing the response according to the plan.
Follow Plan: As an event starts to occur and we start the implementation we should follow the plan we made for that event or the risk. the plan must include all the ways for mitigation of the risk. Risk plan or response plan is a well-documented plan to match the exact situation of the event.
Review Action: Acting on a plan is an important aspect of any project same goes for the response plan hence the team should review the plan and make the changes accordingly can also document it into the risk register.
Reporting and tracking tell about what kind of reporting frequency and format & how risk management process will be audited and documentation of results obtained in risk management process
Moreover, if we talk about risks associated with other project management knowledge areas, the possible sources are cost, schedule, scope, quality, resources and customer satisfaction
The process of planned risk management is highly important and needs to be visited again and again during the change in phases of project life cycle or if there is change in scope as the process is conducted in the very beginning of the project.
Monitor risks-
Monitoring and controlling determines if a triggered event have occurred and appropriate risk plan come into play following the monitoring of changes, if there are any, because changes in project environment can lead to change in probability/impact of an event and also following the viability of risk strategy in a continued fashion.
Monitoring risks involve a list of actions which includes but not limited to-
Looking for occurrence of risk triggers
Determining if the assumptions are still valid
Submitting change requests to change control board
Utilizing the contingency reserves and reshaping the reserves according to changes
Performing various/trend analysis to see the variation from the scope, schedule and cost baselines and predict the future outcomes
Closing out risks
Other important work that cannot be overlooked in the process of monitor risks are the workarounds, risk reassessments, reserve analysis and technical performance analysis
Workarounds are unplanned risk responses which are used when unanticipated events occur in order to put the project back on track matching shoulders with baselines. Project managers who do not spend enough time planning effective risk management, spend a lot of time in performing workarounds.
Risks can be identified during any phase of the project, it is must to continue reviewing risk register and risk management plan to ensure the strategy in case, if it occurs. Every time a new risk is identified the risk register is updated it and readjustments are made to the initial plan if required.
Reserve analysis takes into consideration the both i.e. management reserves and contingency reserves.
Checking reserves is very important in projects to make sure that there are enough funds remaining for the project or not or how much might be needed in order to keep the project safe. Contingency reserves must be used only in response of the expected event in case if it occurs, whereas management reserves are for unforeseen events which were not identified in the beginning during risk identification.
For example, in the case of a website designer leaves the job in BoNA project, the deliverables might be affected in terms of quality and schedule risks. Hence, management will hire an external designer or use third party designer to keep the project on track in terms of schedule and create the good quality deliverable outcomes
Technical performance analysis is conducted to compare planned versus actual completion of technical requirements to determine the variance as any variance might be the originator of a possible threat or an opportunity
The whole monitoring process is logical, and reporting & tracking are performed as per this process
Tracking and reporting on the risk, management process is an integral part to be relied upon in order to make a project successful. It can be conducted by using different kind of matrix which specifies each risk, likelihood of their occurrence, impact if they occur, risk response strategy, trigger event, closure date etc. The use of matrix allows to filter out the risks needed to be looked upon, carefully.
The matrix should be accessible to all the project team members and easy formatted to be understand by all.
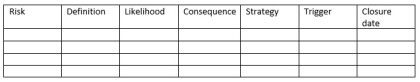
Table Form for Risk Identification
Some organizations use more sophisticated format for monitoring and controlling which allows us to see the Risk status and risk response status, compare the initial likelihood and expected likelihood, initial consequences with expected consequences, actual closure date and other comments on closure activity





Comments (0)