A GUIDE FOR FINANCIAL FRAUD INVESTIGATION & PRECAUTION, SHIVANI SHARMA [read my book txt] 📗

- Author: SHIVANI SHARMA
Book online «A GUIDE FOR FINANCIAL FRAUD INVESTIGATION & PRECAUTION, SHIVANI SHARMA [read my book txt] 📗». Author SHIVANI SHARMA
Companion Virus
This is a type of virus that doesn’t survive without accompanying an existing file or folder. In order to carry out damages, the file or folder being accompanied by companion viruses should be opened or run. Some examples of companion viruses include Terrax.1069, Stator, and Asimov.1539.
Network Virus
Basically, this type of virus spreads out through Local Network Area (LAN) and through the internet. These viruses replicate through shared resources, including drives and folders. When network viruses enter a computer, they look for their potential prey. Dangerous network viruses include Nimda and SQLSlammer.
 Nonresident Virus
Nonresident Virus
Nonresident viruses replicate through modules. When the module is executed, it will select one or more files to infect.
Stealth Virus
Stealth viruses trick antivirus software by appearing like they are real files or programs and by intercepting its requests to the OS. Some antivirus software cannot detect them. Sometimes, it temporarily removes itself from the system without deletion.
Sparse Infector
Sparse infectors use different techniques to minimize its detection. They are viruses that infect “occasionally”. For example, they may only want to infect a program every tenth execution. Because they are occasional infectors, antivirus software has a hard time detecting them.
Spacefiller Virus
Also known as “cavity” viruses, spacefillers attach themselves to the file and can alter the start of the program or change the encrypted code. They also implement stealth techniques so that users cannot determine the increase the file code. The most popular Spacefiller is the Lehigh virus.
FAT Virus
Basically, this type of virus ruins file allocation system where the information about files, including the location, exist.
Others
Other threats are not technically called as “virus”, but they also have the same damaging effects as viruses. This includes worms, adware, malware, Trojan, and ransomware.
To prevent these viruses from affecting your computer, it is important that you install the best and the most competitive antivirus software that can detect, block, and eliminate all types of computer viruses.
Social EngineeringWhat is Social Engineering?
Social engineering is the art of manipulating users of a computing system into revealing confidential information that can be used to gain unauthorized access to a computer system. The term can also include activities such as exploiting human kindness, greed, and curiosity to gain access to restricted access buildings or getting the users to installing backdoor software.
Knowing the tricks used by hackers to trick users into releasing vital login information among others is fundamental in protecting computer systems
In this tutorial, we will introduce you to the common social engineering techniques and how you can come up with security measures to counter them.
Topics covered in this tutorial
How social engineering Works? Common Social Engineering Techniques Social Engineering Counter MeasuresHow social engineering Works?
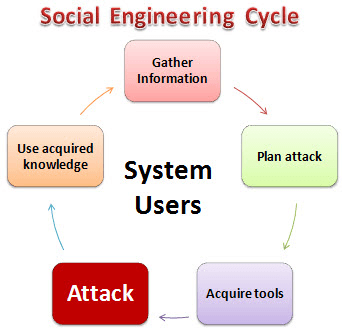
HERE,
Gather Information: This is the first stage, the learns as much as he can about the intended victim. The information is gathered from company websites, other publications and sometimes by talking to the users of the target system. Plan Attack: The attackers outline how he/she intends to execute the attack Acquire Tools: These include computer programs that an attacker will use when launching the attack. Attack: Exploit the weaknesses in the target system. Use acquired knowledge: Information gathered during the social engineering tactics such as pet names, birthdates of the organization founders, etc. is used in attacks such as password guessing.
Common Social Engineering Techniques:
Social engineering techniques can take many forms. The following is the list of the commonly used techniques.
Familiarity Exploit: Users are less suspicious of people they are familiar with. An attacker can familiarize him/herself with the users of the target system prior to the social engineering attack. The attacker may interact with users during meals, when users are smoking he may join, on social events, etc. This makes the attacker familiar to the users. Let’s suppose that the user works in a building that requires an access code or card to gain access; the attacker may follow the users as they enter such places. The users are most like to hold the door open for the attacker to go in as they are familiar with them. The attacker can also ask for answers to questions such as where you met your spouse, the name of your high school math teacher, etc. The users are most likely to reveal answers as they trust the familiar face. This information could be used to hack email accounts and other accounts that ask similar questions if one forgets their password. Intimidating Circumstances: People tend to avoid people who intimidate others around them. Using this technique, the attacker may pretend to have a heated argument on the phone or with an accomplice in the scheme. The attacker may then ask users for information which would be used to compromise the security of the users’ system. The users are most likely give the correct answers just to avoid having a confrontation with the attacker. This technique can also be used to avoid been checked at a security check point. Phishing: This technique uses trickery and deceit to obtain private data from users. The social engineer may try to impersonate a genuine website such as Yahoo and then ask the unsuspecting user to confirm their account name and password. This technique could also be used to get credit card information or any other valuable personal data. Tailgating: This technique involves following users behind as they enter restricted areas. As a human courtesy, the user is most likely to let the social engineer inside the restricted area. Exploiting human curiosity: Using this technique, the social engineer may deliberately drop a virus infected flash disk in an area where the users can easily pick it up. The user will most likely plug the flash disk into the computer. The flash disk may auto run the virus, or the user may be tempted to open a file with a name such as Employees Revaluation Report 2013.docx which may actually be an infected file. Exploiting human greed: Using this technique, the social engineer may lure the user with promises of making a lot of money online by filling in a form and confirm their details using credit card details, etc.Social Engineering Counter Measures
Most techniques employed by social engineers involve manipulating human biases. To counter such techniques, an organization can;
To counter the familiarity exploit, the users must be trained to not substitute familiarity with security measures. Even the people that they are familiar with must prove that they have the authorization to access certain areas and information. To counter intimidating circumstances attacks, users must be trained to identify social engineering techniques that fish for sensitive information and politely say no. To counter phishing techniques, most sites such as Yahoo use secure connections to encrypt data and prove that they are who they claim to be. Checking the URL may help you spot fake sites. Avoid responding to emails that request you to provide personal information. To counter tailgating attacks, users must be trained not to let others use their security clearance to gain access to restricted areas. Each user must use their own access clearance. To counter human curiosity, it’s better to submit picked up flash disks to system administrators who should scan them for viruses or other infection preferably on an isolated machine. To counter techniques that exploit human greed, employees must be trained on the dangers of falling for such scams.Summary
Social engineering is the art of exploiting the human elements to gain access to un-authorized resources. Social engineers use a number of techniques to fool the users into revealing sensitive information. Organizations must have security policies that have social engineering countermeasures.The 16 Most Common Types of Cybercrime Acts
Cybercrime is any criminal activity that takes place in the cyberspace. One of the earliest and the most common types of cybercrime activity is hacking. It roughly started in the 1960s. It involves stealing identities and important information, violating privacy, and committing fraud, among others.
According to the Identity Theft Resource Center, over 170 million personal records were exposed through 780 data security breaches in 2015. The global cost of cybercrime is expected to hit $6 trillion by 2021. 30 to 40% of businesses are affected by cybercrime. From 2017 to 2021, businesses are expected to spend more than $1 trillion for cybersecurity.
Every country in the world has their varied laws and rules against cybercrime activities. In the United States, they have substantive cybercrime laws that prohibit identity theft, hacking, intrusion into computers, and child pornography, among others. In the next section, we will determine the most common types of cybercrime activities.
Most Common Types of Cybercrime Acts
Cybercrime involves the use of computer and network in attacking computers and networks as well. Cybercrime is obviously a criminal offense and is penalized by the law. Cybercriminals devise various strategies and programs to attack computers and systems. These are the most common types of cybercrime acts:
Fraud
Fraud is a general term used to describe a cybercrime that intends to deceive a person in order to gain important data or information. Fraud can be done by altering, destroying, stealing, or suppressing any information to secure unlawful or unfair gain.
 Hacking
Hacking
Hacking involves the partial or complete acquisition of certain functions within a system, network, or website. It also aims to access to important data and information, breaching privacy. Most “hackers” attack corporate and government accounts. There are different types of hacking methods and procedures.
Identity Theft
Identify theft is a specific form of fraud in which cybercriminals steal personal data, including passwords, data about the bank account, credit cards, debit cards, social security, and other sensitive information. Through identity theft, criminals can steal money. According to the U.S. Bureau of Justice Statistics (BJS), more than 1.1 million Americans are victimized by identity theft.
Scamming
Scam happens in a variety of forms. In cyberspace, scamming can be done by offering computer repair, network troubleshooting, and IT support services, forcing users to shell out hundreds of money for cyber problems that do not even exist. Any





Comments (0)